51 | Add to Reading ListSource URL: cs.gmu.eduLanguage: English - Date: 2006-11-29 23:32:26
|
|---|
52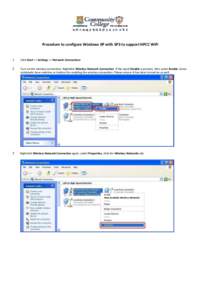 | Add to Reading ListSource URL: hkuspace-plk.hku.hkLanguage: English - Date: 2015-02-11 04:25:27
|
|---|
53 | Add to Reading ListSource URL: www.gov.hkLanguage: English - Date: 2010-02-07 08:35:43
|
|---|
54 | Add to Reading ListSource URL: www.urmc.rochester.eduLanguage: English - Date: 2014-07-10 11:28:23
|
|---|
55 | Add to Reading ListSource URL: download.microsoft.comLanguage: English - Date: 2005-07-07 14:59:26
|
|---|
56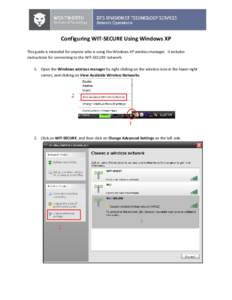 | Add to Reading ListSource URL: www.wit.eduLanguage: English - Date: 2015-01-23 13:37:31
|
|---|
57 | Add to Reading ListSource URL: www.wit.eduLanguage: English - Date: 2015-01-23 13:37:32
|
|---|
58 | Add to Reading ListSource URL: www.vals-asla.chLanguage: English - Date: 2014-01-15 09:12:45
|
|---|
59![Wireless Security’s Future Bruce Potter Cigital, Inc[removed]Ridgetop Circle Suite 400 Wireless Security’s Future Bruce Potter Cigital, Inc[removed]Ridgetop Circle Suite 400](https://www.pdfsearch.io/img/e341c4b04783bb1fae380a8f3a5883f8.jpg) | Add to Reading ListSource URL: www.cigital.comLanguage: English - Date: 2013-11-26 20:44:05
|
|---|
60 | Add to Reading ListSource URL: www.cisco.comLanguage: English |
|---|